Table of Content
- Why Secure SDLC Practices Matter
There’s a familiar pattern many teams fall into. Code gets built, features are rushed out the door, and security checks happen at the very end; usually under pressure to ship. When something slips through, the patchwork begins: emergency fixes, long nights, frustrated customers. We’ve seen this cycle repeat enough times to know it’s not sustainable.
Security doesn’t have to be a last-minute hurdle. Teams that embed secure SDLC practices early on avoid the chaos later. Their software is safer, their releases calmer, and ironically, their delivery often ends up faster. Let’s walk through why that shift matters and what it looks like in practice.
Why Secure SDLC Practices Matter
The Price of Catching Flaws Too Late
Every major breach story has a “what if” moment. What if someone had spotted that flaw during design instead of months after release? The cost difference isn’t small; it’s exponential. According to NIST research, fixing a defect during planning might cost a few hundred dollars. Finding the same issue in production can blow past $30,000, not counting the legal, PR, and customer trust fallout that lingers long after the patch.
|
When a Vulnerability Is Found |
Estimated Cost to Fix |
|
Requirements Stage |
~$100 |
|
Design Stage |
~$500 |
|
Implementation Stage |
~$1,000 |
|
Production |
$30,000+ |
Late fixes are like building a second floor on a crooked foundation; everything above it feels shaky, expensive, and fragile.
Security as a Speed Booster, Not a Brake
There’s still a belief in some teams that security slows things down. The truth is, delays come from last-minute firefighting, not early safeguards. Automated checks, clear coding standards, and reusable secure patterns keep development flowing without unexpected stops. A Forrester study backs this up: teams that adopted secure practices released 20% faster on average while slashing breach risks nearly in half.
Good security feels invisible; it just keeps things moving safely.
Built-In Always Wins Over Bolt-On
Patching a system after it’s shipped is like taping up a cracked pipe after the water’s already flooded the floor. Built-in security stops leaks before they start. When teams plan for threats early, use secure frameworks, and automate checks in every stage, vulnerabilities become harder to introduce in the first place. It’s proactive, not reactive; and it saves both time and sanity.
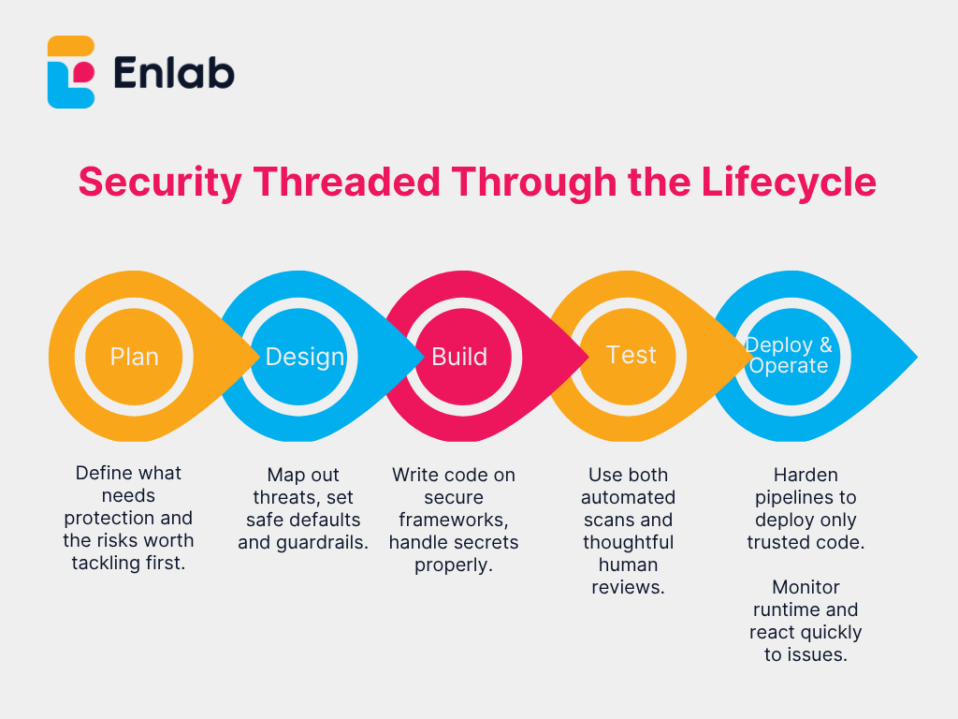
Security Threaded Through the Lifecycle
Security isn’t a single gate or a final checkbox. It’s a thread that runs through every stage of development:
- Plan: Define what needs protection and the risks worth tackling first.
- Design: Map out threats, set safe defaults and guardrails.
- Build: Write code on secure frameworks, handle secrets properly.
- Test: Use both automated scans and thoughtful human reviews.
- Deploy: Harden pipelines so only trusted code goes live.
- Operate: Keep watch on what’s running and respond fast when something looks wrong.
High-performing teams don’t rely on manual sign-offs to enforce these steps. They codify rules into their pipelines. Unsafe configurations or unsigned builds never even make it to deployment. Gartner predicts most organizations will work this way by 2026; catching problems before they ever leave a developer’s laptop.
Building Security into Requirements and Architecture
Threat Modeling That Fits the Sprint
Traditional threat modeling sessions often feel heavy and slow. Modern teams run quick, focused ones instead. During backlog grooming, they ask: What could go wrong? How could this feature be abused if someone tried? Visual tools like OWASP Threat Dragon help map risks fast, and data from Microsoft shows this lightweight approach can cut serious vulnerabilities two- to threefold later in testing.
Classifying Data Early, Avoiding Rework Later
One reason security becomes messy later is that teams don’t define data handling rules upfront. Labeling information; public, internal, sensitive, or regulated; makes encryption and access policies almost automatic. Combine that with guardrails like zero-trust patterns or safe defaults for cloud services, and you avoid the painful re-architecture that happens when “security” gets bolted on after launch.
Making Secure Coding the Default
Frameworks That Keep Mistakes Out
Most developers don’t set out to write insecure code, but mistakes happen when tools don’t guide them. Secure-by-default frameworks, such as Spring Security or ASP.NET Identity, block many common errors before they ever hit code review. IDE plugins that flag risky patterns in real time add another safety net, catching issues while they’re still one keystroke old.
Keeping Secrets Where They Belong
Many breaches trace back to keys or passwords hardcoded into repositories. It’s avoidable. Tools like AWS Secrets Manager or HashiCorp Vault let teams inject credentials safely at build or runtime, removing the chance of accidental leaks altogether.
Reviews That Catch More Than Logic Bugs
Code reviews aren’t just for functionality. A simple security checklist; covering input handling, access controls, and error messages; spots flaws scanners often miss. GitLab’s survey found teams doing this saw 35% fewer security incidents in production. It’s a habit that pays off long after the code merges.
Securing the Software Supply Chain
The modern software stack is a web of dependencies. Open-source packages, third-party APIs, and container images make development faster; but every dependency is a potential backdoor if not managed well. The reality is that attackers increasingly aim for the supply chain because it’s easier to compromise one shared component than to attack every application individually.
SBOMs and Dependency Hygiene
Think of a Software Bill of Materials (SBOM) like an ingredient list for your code. It tells you every library and component in use, where it came from, and its version. Without it, responding to a vulnerability announcement is a guessing game. When Log4Shell hit, teams with SBOMs could instantly identify if they were affected. Others spent days searching codebases, unsure of their exposure.
Good hygiene means:
- Tracking dependencies automatically.
- Avoiding abandoned or unmaintained packages.
- Updating regularly instead of piling up months of risky version drift.
Build Provenance and Artifact Integrity
Even trusted components can be tampered with before they reach you. Verifying where builds come from and how they’re signed ensures nothing malicious sneaks into production. Frameworks like SLSA (Supply-chain Levels for Software Artifacts) are emerging to give teams confidence that their build artifacts are legitimate and traceable.
Hardening the CI/CD Pipeline
Pipelines are the arteries of modern development. If an attacker compromises your CI/CD system, they don’t need to hack the code; they can push their own version straight to production.
Access Control and Guardrails
Limit who can modify pipeline configurations. Use dedicated service accounts with minimal privileges for builds and deployments. Enforce multi-factor authentication and role-based access for sensitive actions like releasing to production.
Automated Security Checks
Make unsafe code fail fast. Policy-as-code tools ensure rules like “no unsigned images,” “no hardcoded credentials,” or “no public S3 buckets” are enforced automatically. These checks prevent insecure builds from slipping through while keeping developers focused on writing features instead of chasing security approvals.
Security Testing That Works With, Not Against, Development
Too often, testing piles up at the end of the cycle, creating a flood of findings right before release. By spreading tests throughout, security feedback becomes faster and less painful.
Choosing the Right Mix
- SAST (Static Analysis): Finds flaws directly in the source code early on.
- DAST (Dynamic Testing): Checks how running applications behave under attack.
- Fuzzing: Bombards the system with unexpected inputs to catch edge-case failures.
A balanced approach avoids over-reliance on one method while catching different categories of vulnerabilities.
Fast Triage and Security Unit Tests
Not every finding needs to stop the release. Automated triage prioritizes the most severe issues. Adding security-focused unit tests ensures that when a vulnerability is fixed, it stays fixed, avoiding regressions in future releases.
Cloud, Infrastructure, and Runtime Protection
Software doesn’t end at deployment. The environment it runs in can introduce its own risks.
Shift-Left for Infrastructure as Code (IaC)
Misconfigured cloud resources are one of the most common breach entry points. Scanning IaC templates for insecure defaults before provisioning prevents public buckets, overly permissive IAM roles, or open database ports from ever being deployed.
Runtime Monitoring and Quick Response
Even with all precautions, things go wrong. Real-time observability tools detect suspicious behavior; unexpected traffic patterns, privilege escalations, or container escapes. A fast incident response plan means teams can contain threats before they escalate into full-blown breaches.
Governance, Metrics, and Building a Security Culture
Security isn’t just tools and scans; it’s a team mindset.
Practical Alignment with Frameworks
Compliance requirements often feel like overhead. Mapping them directly to engineering tasks; using frameworks like OWASP SAMM or NIST SSDF; keeps teams focused on actions that improve real security, not just ticking boxes.
Security Champions and Hands-On Training
Having a “security champion” in each squad bridges the gap between developers and security experts. Pair that with hands-on training; like capture-the-flag sessions or secure coding workshops; and knowledge sticks far better than slide decks ever will.
Metrics That Drive Action
Counting vulnerabilities isn’t enough. Useful metrics show time-to-fix, percentage of builds passing security gates, or reduction in repeated issues. These numbers help teams see progress and keep improving.
A Pragmatic Roadmap for Adopting Secure SDLC Practices
Big changes fail when teams try to do everything at once. The most successful transformations follow a Crawl → Walk → Run approach.
- Crawl: Pick one improvement per lifecycle stage; maybe threat modeling in planning, SBOM generation in builds, and a basic SAST scan in testing.
- Walk: Automate checks, improve coverage, introduce secrets management and signed builds.
- Run: Expand into advanced fuzzing, full policy-as-code enforcement, and continuous security monitoring.
Momentum builds with small wins, and over time, secure practices become the default way of working; not an extra burden.
Conclusion: Making Security the Path of Least Resistance
Secure SDLC isn’t about adding gates or friction. It’s about setting up guardrails that keep teams on track without slowing them down. Small, daily habits; secure coding frameworks, clean dependencies, automated policies; add up to resilient software that’s harder to break and easier to trust.
Every team can start today. Pick one stage of your lifecycle, make a small, meaningful change, and build from there. Security becomes natural when it’s woven into the fabric of development, not bolted on after the fact.
References:
NIST Report on Software Security Costs, NIST, 2024
DevOps 2030: People, Practices, And Platformsm, Forrester, 2022
HashiCorp State of Cloud Strategy Survey 2024: Forrester’s key recommendations, Hashicorp, 2024
Gartner Says 30% of Enterprises Will Automate More Than Half of Their Network Activities by 2026, Gartner, 2024
GitLab survey highlights wins, challenges as orgs adopt DevSecOps, Gitlab, 2023